




Published on Feb 14, 2025
An embedded system is a special-purpose computer system, which is completely encapsulated in the device it controls. It has specific requirements and performs pre-defined tasks, unlike a general-purpose personal computer. PDAs, mobile phones, household appliances, monitoring and control systems for industrial automation etc are examples embedded systems.
Even though the technology of embedded systems is fast improving and devices are becoming more and more advanced very less attention is being given to its security. The reason mainly being the high sensitivity of costs, even a small rise in cost of production will make a big difference when building millions of units.
Embedded systems often have significant energy constraints, and many are battery powered. Some embedded systems can get a fresh battery charge daily, but others must last months or years on a single battery.
Protection of an embedded system is very intricate from that of a typical computer because of the working environments of the particular system. Building a secure embedded system also involves designing a robust application that can deal with internal failures; no level of security is useful if the system crashes and is rendered unusable. It is obvious that the higher the level of security the bigger the cost of the product. For this reason the manufacturer should carry out a risk analysis to determine what the cost of a successful attack against his product will be and what class of attacker he must protect the product from. Once he knows the possible loss he must identify the candidate security measures for completion and their cost.
Whenever a system has to communicate with another device the data passes through a number of untrusted intermediate points. Therefore the secure data must be scrambled in such a way that the data will be useless or unintelligible for anyone who is having unauthorized access to the secure data. This can be achieved with the help of cryptographic methods, Digital Signatures and Digital Certificates.
Encryption is the process of scrambling/encrypting any amount of data using a (secret) key so that only the recipient, who is having access to the key, will be able to decrypt the data. The algorithm used for the encryption can be any publicly available algorithm like DES, 3DES or AES or any algorithm proprietary to the device manufacturer.
The Data Encryption Standard (DES) is a block cipher (a method for encrypting information) .It is based on a Symmetric-key algorithm that uses a 56-bit key. An algorithm that takes a fixed-length string of plain text bits and transforms it through a series of complicated operations into another cipher text bit string of the same length. In the case of DES, the block size is 64 bits. DES uses a key to customize the transformation, so that decryption can supposedly only be performed by those who know the particular key used to encrypt. The key ostensibly consists of 64 bits; however, only 56 of these are actually used by the algorithm. Eight bits are used solely for checking parity, and are thereafter discarded. Hence the effective key length is 56 bits.
If publicly available algorithms are used, the security of the transferred data totally depends on the secrecy of the keys used for the encryption.
Key agreement algorithms exchange some public information between two parties so they each can calculate a shared secret key. However, they do not exchange enough information that eavesdroppers on the conversation can calculate the same shared key. Key agreement algorithm will have a private-key and an associated public-key. The private-key is generally a random number of hundreds or few thousands of bits and the public-keys are derived from the private-key using the one-way function specified by the key agreement algorithm.
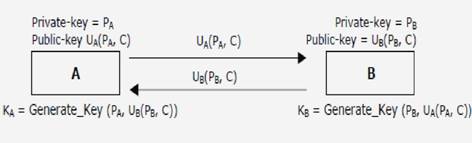
The key generation algorithm 'Generate Key' will be such that the generated keys at the device A and B will be the same, that is shared secret KA=KB=K(PA, PB, C).
This protocol faces a deficiency. Nothing in this key agreement protocol prevents someone from impersonating.. So even though the transmissions of the public keys do not need to be encrypted, they should be signed for maximum safety.
As mentioned before, public-key cryptography is inefficient. In order to make public-key authentication practical, the digital signature was invented. A digital signature is simply a hash of the data to be sent encrypted using the public-key authentication method. Some digital signature algorithms DSA, Full Domain Hash, RSA-PSS, etc.
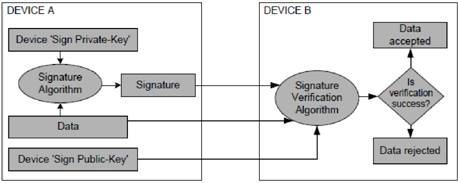
Fig 2 Digital signature algorithm
For establishing shared secret using the key agreement algorithm, it is important for device to receive an authenticated public-key from the peer. For authenticated exchange of public-key, Digital Signature is used. By encrypting only the fixed-size message hash, we remove the inefficiency of the public-key algorithm and we can efficiently authenticate any arbitrary amount of data.
In digital signature, like the key agreement algorithm, a device uses a pair of keys,
'sign private-key' and 'sign public-key'. Only the device knows its sign private-key whereas the sign public-key is distributed to all the communicating devices.
A device signs the message using a signatures algorithm with its sign private-key to generate a signature and any device that has got the access to the sign public-key of the signed device can verify the data with the signature using the signature verification algorithm. If any third party modifies the data or signature, the verification fails.
Even while using the digital signature algorithm, the 'sign public-key' from a peer device has to be obtained by an authenticated way to ensure the authenticity of a received message. For key agreement or digital signature the authenticated transfer of public-key n a large network is difficult or even not possible without a centralized trusted authority. This centralized authority is trusted by all the devices in the network. This authority is generally known as trusted Certificate Authority or CA. The Certificate Authority (CA) signs the public-keys of devices along with the device ID using the CA's private-key to generate the signature. Security Needs Within The Device
Security is not all about encryption. It's also about policy, procedure, and implementation. Case in point, encryption based on a secret key is only as good as the policy that controls access to the key. Secure code alone does not make a secure system. Security must be considered at each phase of the process, from requirements to design to testing, and even support.
Whether it is the private-key of any public-key algorithm or it is any previously negotiated shared secret between the devices, the security of data transferred depends in the secrecy of these keys. These secret keys and secret values stored in the device (some even for the lifetime of the device.) that requires protection from unauthorized exposure. Hardware and software security measures implemented in the device must defeat any attempts of unauthorized access to retrieve these secret keys
1. Jesús Lizarraga, Roberto Uribeetxeberria, Urko Zurutuza, Miguel Fernández SECURITY IN EMBEDDED SYSTEMS Computer Science Department Mondragon University, Spain.
2. Lawrence Ricci (eMVP) Larry McGinnes (CPL) Applied Data Systems COACT White Paper Embedded System Security Designing Secure Systems with Windows CE
3. www. ieeexplore.ieee.org
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |