




Published on Apr 02, 2024
Underwater wireless communication networks (UWCNs) include sensors and autonomous underwater vehicles (AUVs) that interact to perform specific applications such as underwater monitoring. Coordination and information sharing between sensors and AUVs make the provision of security challenging.
The unique characteristics of the underwater acoustic channel and the differences between such networks and their ground based counterparts require the development of efficient and reliable security mechanisms.
The aquatic environment is particularly vulnerable to malicious attacks due to the high bit error rates, large and variable propagation delay, low bandwidth of acoustic channels in water. Achieving reliable inter vehicle and sensor-AUV communication is especially difficult due to the mobility of AUVs and the movement of sensors with water currents.
The above mentioned characteristics of UWCNs have several security issues associated like packet errors, eavesdropping, modification of packets, and many more. Also since power consumption in underwater communications is higher than in terrestrial radio communications energy exhaustion attacks can reduce network life.
The different attacks possible are Jamming, Wormholes, Selective Forwarding, Sybil Attacks, etc. Defences for these are discussed. Jamming can be overcome by Spread Spectrum techniques, Wormhole detection is done with a visual modelling using Dis-VoW and other attacks can be countered by authentication, verification, and positioning.
Open research challenges for secure localization, routing and time synchronization are mentioned.
In this paper UWCNs is discussed, with emphasis on the possible attacks, countermeasures and further opportunities and scope for development in this direction to improve security of such networks.
Underwater wireless communication networks (UWCNs) consist of sensors and autonomous underwater vehicles (AUVs) that interact, coordinate and share information with each other to carry out sensing and monitoring functions. A pictorial representation is shown below:
In last several years, underwater communication network (UWCN) has found an increasing use in a widespread range of applications, such as coastal surveillance systems, environmental research, autonomous underwater vehicle (AUV) operation, oil-rig maintenance, collection of data for water monitoring, linking submarines to land, to name a few.
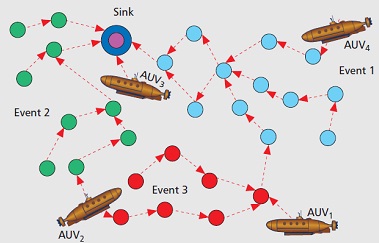
By deploying a distributed and scalable sensor network in a 3-dimensional underwater space, each underwater sensor can monitor and detect environmental parameters and events locally. Hence, compared with remote sensing, UWCNs provide a better sensing and surveillance technology to acquire better data to understand the spatial and temporal complexities of underwater environments. Present underwater communication systems involve the transmission of information in the form of sound, electromagnetic (EM), or optical waves. Each of these techniques has advantages and limitations.
Based on applications there are three types of UWSNs (sensor networks):
1) Mobile UWSNs for long-term non-time critical applications (M-LT-UWSNs);
2) Static UWSNs for long-term non-time critical applications (S-LT-UWSNs);
3) Mobile UWSNs for short-term time-critical applications (M-ST-UWSNs).
Besides the UWSNs mentioned above, underwater networks also include sparse mobile AUV (autonomous underwater vehicle) or UUV (unmanned underwater vehicle) networks, where vehicles/nodes can be spaced out by several kilometres. These types of networks have their unique communication requirements.
Among the three types of waves, acoustic waves are used as the primary carrier for underwater wireless communication systems due to the relatively low absorption in underwater environments.
The security requirements to be met in UWCNs are:
• Authentication: Authentication is the proof that the data received was sent by a legitimate sender. This is essential in military and safety-critical applications of UWCNs.
• Confidentiality: Confidentiality means that information is not accessible to unauthorized third parties. It needs to be guaranteed in critical applications such as maritime surveillance.
• Integrity: It ensures that information has not been altered by any adversary. Many underwater sensor applications for environmental preservation, such as water quality monitoring, rely on the integrity of information.
Availability: The data should be available when needed by an authorized user. Lack of availability due to denial-of-service attacks would especially affect time-critical aquatic exploration applications such as prediction of seaquakes.
• Attack: Attempt to gain unauthorized access to a service, resource, or information, or the attempt to compromise integrity, availability, or confidentiality.
• Attacker, Intruder, Adversary : The originator of an attack.
• Vulnerability : Weakness in system security design, implementation, or limitations that could be exploited.
• Threat : Any circumstance or event (such as the existence of an attacker and vulnerabilities) with the potential to adversely impact a system through a security breach.
Defence : An idea or system or model that counters an attack Jamming and Spread Spectrum Technique to Counter Jamming
Jamming is deliberate interference with radio reception to deny the target's use of a communication channel. For single-frequency networks, it is simple and effective, rendering the jammed node unable to communicate or coordinate with others in the network.
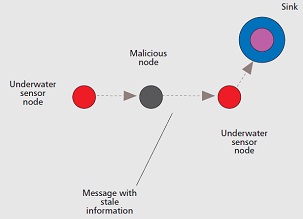
A jamming attack consists of interfering with the physical channel by putting up carriers on the frequencies used by nodes to communicate. Since it requires a lot of energy, attackers usually attack in sporadic bursts. Since underwater acoustic frequency bands are narrow (from a few to hundreds of kilohertz), UWCNs are vulnerable to narrowband jamming. Localization is affected by the replay attack when the attacker jams the communication between a sender and a receiver, and later replays the same message with stale information (an incorrect reference) posing as the sender.
In frequency hopping, a device transmits a signal on a frequency for a short period of time, changes to a different frequency and repeats. The transmitter and receiver must be coordinated. Direct-sequence spreads the signal over a wide band, using a pseudo-random bit stream. A receiver must know the spreading code to distinguish the signal from noise.
Frequency-hopping schemes are somewhat resistant to interference from an attacker who does not know the hopping sequence. However, the attacker may be able to jam a wide band of the spectrum, or even follow the hopping sequence by scanning for the next transmission and quickly tuning the transmitter.
1. Mari Carmen Domingo, “Securing Underwater Wireless Communication Networks”, IEEE Wireless Communications, February 2011
2. W. Wang, J. Kong, B. Bhargava and M. Gerla, “Visualization of Wormholes in Underwater Sensor Networks: A Distributed Approach”, International Journal of Security and Networks, vol. 3, no. 1, 2008, pp. 10–23.
3. www. ieeexplore.ieee.org
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |