




Published on Apr 02, 2024
In the era of technology, the voting machine, which is present today, is highly unsecured. Being in the age of Computers we are compromising the security by opting for Electronic voting machine because in the present electronic voting machine is not intelligent that is it cannot determine the person came for the voting is eligible or not .
That mean the whole control is kept in the hand of voting in charge officer. One more risk with the present voting machine is that any body can increase the vote count, since the count is present in the machine itself.
In proposed machine that is "Global Wireless E-Voting ", the machine is made intelligent which can determine the eligibility of the voter by scanning the eye pattern and also the vote count is not kept into the same machine itself instead of it it is store in the remote server by converting it into radio waves. Here there is no chance of increasing the vote count of machine. Even in case of damage to voting machine there will not be harm to continuity of the election process.
• In our system we trying to keep counting of votes in to a remote secured system
• In Global Wireless E-Voting system we are using a electronic circuit which enable the voter to vote and transfer this vote to the remote system by converting it to radio wave through the mobile towers.
• Global Wireless E-Voting machine can check the eligibility of the candidate by itself, so there is no question of corruption. Machine itself is automated to check the eligibility of the candidates.
• Here we need not to go for the re election even if the machine is damaged.
• A person even can vote from a mobile system and also from Internet.
• We can vote from any where even though being a voter of another region.
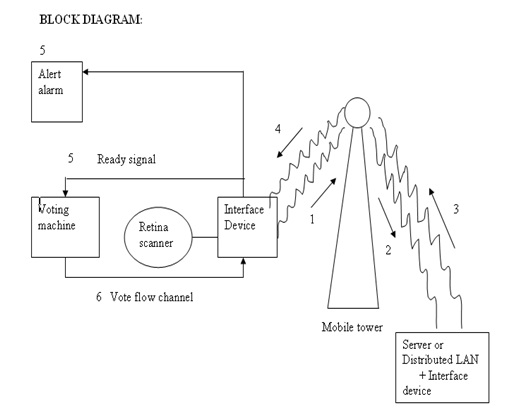
Whenever voters enter to voting booth then he will be instructed to directly look at retina scanning machine at this time the machine scans the retina. once retina scanning properly confirmed then it sent signal to the voting machine as to accept the vote it will be powered on .then voter is made to vote. Now the whole data including the retina pattern is sent to interfacing device which convert into radio waves of mobile frequency range and these radio waves are sent to mobile tower and then to the remote server, where the authentication and voters identification is stored into a secured database.
The received data is first converted into digital format from the radio waves through the interface device kept at the server side, and then retina pattern and vote separated.
Next the retina pattern is matched against the existing database .If match is found then flag is check which indicates its voting status i.e. if the voter is not voted yet then +ve ack is send to the mobile tower and then to the corresponding voting machine. This ack is recognized by the receiver kept at the voter side and machine is made to scan next retina pattern and vote, otherwise if -ve ack then alert alarm is made to ring.
• A voting system should satisfy these requirements
• Eligibility and authentication – only registered voters must be admitted.
• Uniqueness – no voter may cast his vote more than once.
• Accuracy – voting systems should record the votes correctly.
• Verifiability and audit ability – it should be possible to verify that all votes
• have been correctly accounted for in the final tally, and there should be
• reliable and verifiably authentic election records.
• Secrecy – no one should be able to determine how any individual voted.
• Non-coerciability – voters should not be able to prove to others how they
• voted; otherwise vote selling and coercion would be facilitated.
• Minimum skill requirement for voter
• Minimal requirement of equipment
• Minimum Time required for vote
There are several more issues that we have to consider along the Implementation such as
Security
Efficiency
Geographical Problems
The radio waves of a mobile frequency consist of Retina pattern and vote can be generated by means of external source. That’s why we need to provide some sot of security to avoid this problem. One of the idea to solve this problem is CDMA (which will be explained later ) and another technique is inserting security bits at regular interval of time during the transmission of radio waves (Ex.2 msec) .At the server side after the given interval (2 msec ) security bits are checked (ex 1001) . In case of positive confirmation we can accept as valid vote, other wise simply rejected.
Another problem is that one may trap the radio waves in between and can determine the person and the vote; this may disclose the result of the election before the completion of the voting process. To avoid this problem we can go for applying the efficient and complex encryption algorithm so that the transparency of data can be hidden and the server side the encrypted data can be again decrypted and original data can retrieved this make the trapping of wave meaningless
Whenever the data which is sent from the voter (client) side, it is in the large amount, this delays a bit a voting system and the data that is received at server side is in the ccess mode i.e. more than one client is sending the data. To over come this problem the following
1. Applying compression Algorithms at the Client and server side so those to decrease the data transfer. Compression technique such as JPEG compression or any other Compression.
2. Instead of using single server PC we will go for distributed Operating system environment with multiple servers. This makes the job sharing and processing faster which leads to fast responds in case of Multiple Access Environment
3. To solve the concurrency problem in case of Multiple access environment we will use CDMA technique.
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |