




Published on Nov 30, 2023
Automated Parking System using RFID Technology Project is mainly based on the RFID technology. There has been a considerable amount of reduction in transaction costs and decrease in stock shortage with the use of Radio Frequency Identification (RFID) technology in automation. Most of the RFID networks include a wide range of automation technologies.
These technologies are RFID readers, RFID writers, RFID barcode scanners, and RFID controllers. In this study, a solution has been provided for the problems encountered in parking-lot management systems via RFID technology. RFID readers, RFID labels, computers, barriers and software are used as for the main components of the RFID technology.
The software has been handled for the management, controlling, and operation tasks for parking lots. Check-ins and check-outs of the parking-lots will be under control with RFID readers, labels and barriers. Check-ins and check-outs will be handled in a fast manner without having to stop the cars so that traffic jam problem will be avoided during these processes
Since there won't be any waiting during check-ins and check-outs the formation of emission gas as a result of such waiting will be avoided. Therefore, by this project we develop a parking system for an organization to have automated parking system for making best use of space, decreasing the man power and providing authentication for the vehicles from avoiding the theft.
1. RFID active tags can be affixed to vehicles for activating hands-free access to communities and parking lots.
2. The RFID reader can also trigger surveillance cameras or video recorders whenever a vehicle enters or exits the controlled area.
1. Provides full inventory history of cars at each location,
2. Enables full control of inventory content and location for cars in the facility,
3. Gives automatic notification when a car enters or leaves the lot,
4. Initiates an alarm when an unauthorized vehicle enters or leaves the lot,
5. Eliminates manual record keeping, thereby increasing accuracy and staff productivity.
It provides check-ins and check-outs of the vehicles at the parking place. The person who is entering the parking area his or the vehicles information is read by the RFID reader, the RFID then checks the database to see whether is a registered person or not and the barrier gets opened by allotting a slot to park his vehicle. Checkin time of the vehicle is noted. When he is checking out of the place the check time of the vehicle is noted and the vehicle is authenticated with his ID card. Suppose an unauthorized user is taking the vehicle, then the barrier doesn`t get opened. No vehicle can be parked without registering with the organization. Only the persons who had registered their vehicles with the organization can only park.
1. Computes data and facts about the vehicles entering and exiting the parking area, (This includes the time of entry, date of entry and the amount that the customer is subjected to pay as per the parked hours)
2. User friendly, easy to operate.
3. Time saving: eliminates lines and traffic jams on both entrance and exit, response time under 1 sec.
4. Special reserved parking for staff etc.
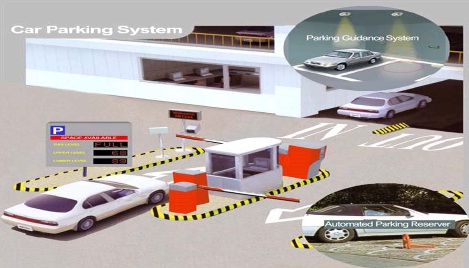
diagram that shows how processes operate with one another and in what order. It is a construct of a Message Sequence Chart. A sequence diagram shows object interactions arranged in time sequence. It depicts the objects and classes involved in the scenario and the sequence of messages exchanged between the objects needed to carry out the functionality of the scenario. Sequence diagrams typically are associated with use case realizations in the Logical View of the system under development. A sequence diagram shows, as parallel vertical lines (lifelines), different processes or objects that live simultaneously, and, as horizontal arrows, the messages exchanged between them, in the order in which they occur. This allows the specification of simple runtime scenarios in a graphical manner.
An organization's technical staff can find sequence diagrams useful in documenting how a future system should behave. During the design phase, architects and developers can use the diagram to force out the system's object interactions, thus fleshing out overall system design. One of the primary uses of sequence diagrams is in the transition from requirements expressed as use cases to the next and more formal level of refinement. Use cases are often refined into one or more sequence diagrams. In addition to their use in designing new systems, sequence diagrams can be used to document how objects in an existing (call it "legacy") system currently interact. This documentation is very useful when transitioning a system to another person or organization
The sequence diagram of this card shows how the AADHAR PLUS card works and the steps involved in it. The user is first checked for authorization and if the authorization is correct then only the access will be provided to the user. This authorization is done with the help of a password. This password will be separate for each and every user. In case of Medical Details, this authorization is not required.
As in case of an emergency it will not be possible for any user to provide authentication. Thus this module does not need authentication at all. But the other modules will need authentication as for the security reasons. So that the passport and driving license details are safe and there is no unauthorized or illegal use of those details and in case of smart parking also for keeping our e cash safe we have the password facility so that in case of lost card or theft, there should not be any misuse of the card and so this will help to keep the details safe and secured. The given sequence diagram explains in what sequence and the way the card works, authentication and other processes.
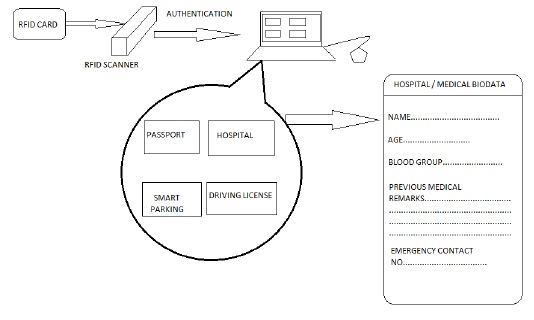
The above shown diagram is a working model. It shows how the RFID SCANNER reads the RFID TAG/CARD and the signal is given to the PC and the modules will be shown. The computer displays four modules which are shown in above diagram and in the right hand side a demo is shown, when we click in the Hospital button it will display another form which will be like the above given demo which will have all the necessary hospital details and all. The same way it will work for each and every module.
In this project work the RFID car parking system is designed and tested using the simulated environment of Visual Studio IDE compiler. This RFID car parking system will be useful to develop automated parking system which enroll the vehicle that pass through without the presence of the security officer, if there occurs any un authorized access in car parking area, alarm will be enabled automatically by the system by checking the ID provide to the users and their cars. Hence the set up is simulated and tested for correctness. This project will be a boon to all departments.
This project can be enhanced for tracking the vehicle speed on the roads and to differentiate the vehicles from VIPs and staff and allowing the vehicles to trace them in the restricted area.
The two most common types of RFID tag frequencies that are used are low and high frequencies and they are the Active and Passive RFID. Although they both fall under the “RFID” moniker and are often discussed interchangeably, Active RFID and Passive RFID are fundamentally different technologies. While both uses radio frequency energy to communicate between a tag and a reader, the method of powering the tags is different. Active RFID uses an internal power source (battery) within the tag to continuously power the tag and its RF communication circuitry, whereas Passive RFID relies on RF energy transferred from the reader to the tag to power the tag.
1) reflects energy from the reader or
2) absorbs and temporarily stores a very small amount of energy from the reader’s signal to generate its own quick response.
In either case, Passive RFID operation requires very strong signals from the reader, and the signal strength returned from the tag is constrained to very low levels by the limited energy. This will be the great limitation.