




Published on Nov 30, 2023
Biometric readings, which range from several hundred bytes to over a megabyte, have the advantage that their information content is usually higher than that of a password or a pass phrase. Simply extending the length of passwords to get equivalent bit strength presents significant usability problems.
It is nearly impossible to remember a 2K phrase, and it would take an annoyingly long time to type such a phrase (especially without errors). Fortunately, automated biometrics can provide the security advantages of long passwords while retaining the speed and characteristic simplicity of short passwords.
Even though automated biometrics can help alleviate the problems associated with the existing methods of user authentication, hackers will still find there are weak points in the system, vulnerable to attack. Password systems are prone to brute force dictionary attacks. Biometric systems, on the other hand, require substantially more effort for mounting such an attack. Yet there are several new types of attacks possible in the biometrics domain. This may not apply if biometrics is used as a supervised authentication tool. But in remote, unattended applications, such as Web-based e-commerce applications, hackers may have the opportunity and enough time to make several attempts, or even physically violate the integrity of a remote client, before detection.
A key factor in the selection of the appropriate biometric technology is its accuracy. Biometric accuracy is the system's ability of separating legitimate matches from imposters. When the live biometric template is compared to the stored biometric template, a matching score is used to confirm or deny the identity of the user. System designers set this numeric score to accommodate the desired level of accuracy for the system, as measured by the False Acceptance Rate (FAR) and False Rejection Rate (FRR).
. False Rejection Rate (FRR) refers to the statistical probability that the biometric system is not able to verify the legitimate claimed identity of an enrolled person, or fails to identify an enrolled person.
. False Acceptance Rate (FAR) refers to the statistical probability of False Acceptance or incorrect verification. In the most common context, both False Rejection and False Acceptance represent a security hazard.
If a mismatching pair of fingerprints is accepted as a match, it is called a false accept. On the other hand, if a matching pair of fingerprints is rejected by the system, it is called a false reject. The error rates are a function of the threshold. Often the interplay between the two errors is presented by plotting FAR against FRR with the decision threshold as the free variable. This plot is called the ROC (Receiver Operating Characteristic) curve. The two errors are complementary in the sense that if one makes an effort to lower one of the errors by varying the threshold, the other error rate automatically increases. In a biometric authentication system, the relative false accept and false reject rates can be set by choosing a particular operating point (i.e., a detection threshold). Very low (close to zero) error rates for both errors ( FAR and FRR ) at the same time are not possible. By setting a high threshold, the FAR error can be close to zero, and similarly by setting a significantly low threshold, the FRR rate can be close to zero. A meaningful operating point for the threshold is decided based on the application requirements, and the FAR versus FRR error rates at that operating point may be quite different. To provide high security, biometric systems operate at a low FAR instead of the commonly recommended equal error rate ( EER ) operating point where FAR=FRR .
Fingerprints are a distinctive feature and remain invariant over the lifetime of a subject, except for cuts and bruises. As the first step in the authentication process, a fingerprint impression is acquired, typically using an inkless scanner. Several such scanning technologies are available. Figure 5A shows a fingerprint obtained with a scanner using an optical sensor. A typical scanner digitizes the fingerprint impression at 500 dots per inch (dpi) with 256 gray levels per pixel. The digital image of the fingerprint includes several unique features in terms of ridge bifurcations and ridge endings, collectively referred to as minutiae.
There are two ways a matching algorithm can be implemented, using either identification matching or authentication matching. In identification matching, one fingerprint is compared to many fingerprints using an Automated Fingerprint Identification System (AFIS) that is comprised of several computers and a database storage system. In authentication matching, where there is a “one to one” fingerprint comparison, there needs to be only one fingerprint terminal and a token loaded that contains the fingerprint template. The matching could be done on token, in the terminal or in both the terminal and token.
5.3.1 The Sensors
Electronic fingerprint sensors are manufactured in different ways using capacitive, optical, thermal, or pressure sensitive (resistive) technology. These different types of sensors are able to produce an image of the fingerprint when the ridge is darker than the valley. The most common sensors currently on the market are capacitive and optical sensors. Optical sensors provide the best image quality but are expensive and can be fooled by some fake fingers. Sensors based on capacitive technology provide a balance of image quality and cost although, some fake fingers can also fool this technology. However, the most common fake fingers made of silicon cannot fool a capacitive sensor because the fake finger does not possess electrical properties.
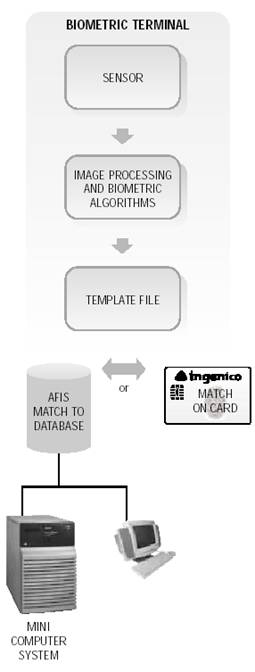
Figure 5.4 Components of a fingerprint system
Iris recognition leverages the unique features of the human iris to provide an unmatched identification technology. So accurate are the algorithms used in iris recognition that the entire planet could be enrolled in an iris database with only a small chance of false acceptance or false rejection. The technology also addresses the FTE (Failure To Enroll) problems, which lessen the effectiveness of other biometrics. The tremendous accuracy of iris recognition allows it, in many ways, to stand apart from other biometric technologies. All iris recognition technology is based on research and patents
held by Dr. John Daugman.
Iris recognition is based on visible (via regular and/or infrared light) qualities of the iris. A primary visible characteristic is the trabecular meshwork (permanently formed by the 8th month of gestation), a tissue that gives the appearance of dividing the iris in a radial fashion. Other visible characteristics include rings, furrows, freckles, and the corona, to cite only the more familiar. Expressed simply, iris recognition technology converts these visible characteristics into a 512 byte IrisCode(tm), a template stored for future verification attempts. 512 bytes is a fairly compact size for a biometric template, but the quantity of information derived from the iris is massive.
From the iris' 11mm diameter, Dr. Daugman's algorithms provide 3.4 bits of data per square mm. This density of information is such that each iris can be said to have 266 unique "spots", as opposed to 13-60 for traditional biometric technologies. This '266' measurement is cited in all iris recognition literature; after allowing for the algorithm's correlative functions and for characteristics inherent to most human eyes, Dr. Daugman concludes that 173 "independent binary degrees-of-freedom" can be extracted from his algorithm – an exceptionally large number for a biometric.
| Are you interested in this topic.Then mail to us immediately to get the full report.
email :- contactv2@gmail.com |